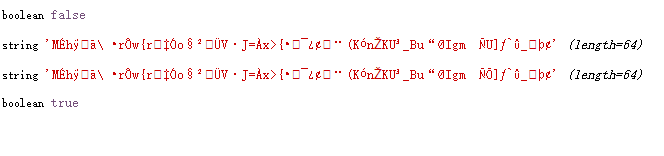md5强类型比较的绕过
$a = '%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a...
攻防世界-Normal_RSA
这题是关于RSA解密相关的,下载题目文件后压缩包里有两个文件,分别是公钥和加密的文件,我们的思路就是通过公钥爆破出私钥,再根据私钥解密出密文其中 .pem格式的是openssl的文件类型,所以我们需要用到openssl来解出RSA中的N 值与 e值,这个过程完全是可计算的,并不是爆破,毕竟传统的rsa公钥是(e,N)的形式,这里只是通过openssl把他格式化了一下kali自带有openss...
CTF-web 快速计算
题目描述:快速口算分值: 350小明要参加一个高技能比赛,要求每个人都要能够快速口算四则运算,2秒钟之内就能够得到结果,但是小明就是一个小学生没有经过特殊的培训,那小明能否通过快速口算测验呢?平台题目地址做题地址这个无论是直接手算或者发送到BURP上都不能完成,所以我写了个py脚本,可以一键拿keyimport requests from lxml import etree """发送请求...
CTF-MD5碰撞
title: CTF-MD5碰撞categories: CTFtags: [MD5]date: 2020-01-15 11:02:18<p style="text-align: left;">0x00:今天天气寒冷,但是再严峻的天气也不能阻挡本屌爱学习的热心,按照国际惯例困了累了做CTF题,于是乎遇到下面这道题</p><!-- wp:imag...